In the sudden shift to working from home, many organisations have found themselves reliant on employees using unsecured personal devices and internet access. A BYOD Policy is a critical step in mitigating the cyber risk this poses.
The Covid-19 pandemic has pushed organisations to suddenly allow working from home by employees who had not previously worked remotely and who were not equipped with corporate devices or access technologies.
The speed of the shift to large scale remote work has resulted in the use of personal devices including mobile phones, laptops, tablets, desktops, USBs and printers. Some employees are also using personal WiFi internet connections to access the corporate network.
To mitigate the risk of this BYOD shift, it is critical that organisations provide employees with a BYOD Policy that sets clear expectations for behaviour.
Organisations can follow a few key steps to create or expand a BYOD policy to enable secure and productive remote work on mobile devices during the pandemic.
1. Why is a Covid-19 BYOD policy essential ?
Organisations that don't already have a BYOD policy in place must create one if they have employees working remotely on personal devices. Managers and executives can't simply tell employees that everything is fine and they can use any mobile device for work purposes. There must be a policy in place that promotes the interests of the company; and protects the safety and productivity of individual employees.
Furthermore without one, a company could be
- failing in its legal responsibility to apply due diligence to workplace practice (even when the workplace is at home)
- risking the loss of commercially sensitive information or intellectual property
- risking commercial loss if systems are compromised or cyber criminals install malware or ransomware
- risking reputational loss

2. What does a Covid-19 BYOD policy need to include?
A BYOD policy needs to regulate in favour of behaviours that protect the safety of the employee and the company; including the safe-guarding of identity, reputation, and data; and providing cost control.
More specifically a BYOD policy will include:
- which employees are permitted to use personal devices for corporate business and to access the corporate network
- any restriction on the range of personal devices that may be used for corporate business
- the applications or collaboration tools that are available to employees to utilise on their personal devices
- any corporate network access restrictions
- how devices will be secured
- how data will be secured
- the employer’s rights in respect of access to data and information contained on personal devices
- the responsibility for technical support in respect of devices or network access
- how the various risks associated with the use of personal devices are shared and are mitigated

3. How to implement BYOD security measures
IT leaders can't simply assume that employees will implement security measures on their own. Nor should employees be expected to, or be relied upon to do so.
Asking users to implement security measures will put the organisation at a major risk for security breaches and malware attacks.
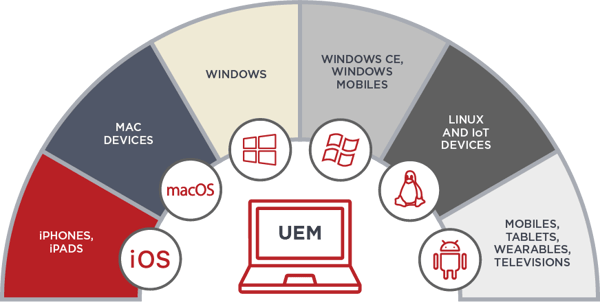
Two of the most powerful tools organisations can deploy in this remote working environment are Unified Endpoint Management, UEM - also historically referred to as EMM or MDM; and Mobile Threat Defence MTD.
UEM manages an enterprises’ mobile devices, applications and content. MTD detects and responds to threats at the device and network layers.
Unified Endpoint Management is baseline
No BYOD mobile device should connect to corporate systems without UEM control
For employees using personal devices, IT leaders should enforce all BYOD policies with a unified endpoint management (UEM) platform that can manage connectivity and security-related endpoint risks.
With UEM, organisations can:
- enforce security policies like multi-factor authentication and password protection
- push security patches and software updates
- manage access to the corporate network blocking devices which are not compliant with security policy
- block specific applications or websites from being downloaded on the device
- lock or wipe a compromised device
- set-up containerisation to separate corporate and personal workspaces and data
- remote management of devices
Should the organisation decide to replace personal devices with corporate-owned devices, UEM also provides benefits in zero-touch deployment of devices to end users.
Mobile Threat Defence complements UEM
As users move outside the perimeter the endpoint becomes the top vector of attack.
A MTD product complements a UEM environment. Leading vendors, VMware and Intune, integrate with the leading MTD vendors, like Wandera, to provide additional security and cost control features in three main areas.
- Zero-Trust Private Network Access
Moving beyond the device to enforce security at the application and network layers, and offers more granulated network protection by applying a zero-trust access policy. This is particularly important in the Covid remote working era as it provides users with the flexibility to work any time, anywhere with secure remote access – for unmanaged and BYOD devices.- next-gen encryption and networking protocols
- identity-based micro-tunnels secure your corporate apps
- protect sensitive data with adaptive access such as device risk posture and location
- integrate IdP and UEM for enhanced management, or SIEM and SOAR for greater visibility
- zero latency issues by eliminating unnecessary traffic backhauling
- silent device authentication or seamless access via SSO
- avoids requirement to re-authenticate every time
- configure least-privilege access for applications individually with granular controls
- review security with real-time event visibility and easily audit logs
- Threat Detection and Defence
Protect against all cyber threats, from device vulnerabilities to phishing to malicious or risky apps, with multi-level cloud and endpoint security. Manage risks with zero-day advanced threat intelligence.- monitor endpoints for vulnerabilities, from escalated privileges to outdated OS's.
- perform continuous app risk assessments for advanced detection of malware and risky applications.
- detect man-in-the-middle attacks and open a fail-safe VPN tunnel to ensure business continuity.
- protect against known and zero-day phishing threats.
- stop malicious downloads and connections to third-party app stores. Prevent data ex-filtration and command-and-control attacks.
- monitor for data leaks and prevent sensitive data loss. Safeguard user privacy with added encryption
- Data Compliance Policy
Some leading MTD vendors, such as Wandera, also include a data compliance functionality in their product suite. It will- enforce acceptable online behavior with intelligent content filtering rules.
- mitigate legal exposure from non-compliant or illicit use.
- prevent sensitive corporate data from being exposed on personally enabled cloud apps.
- block unsanctioned services via the browser and application.
- provide visibility of data consumption with real-time analytics and detailed reporting.
- prevent bill shock by capping and limiting non-business data usage.
- reduce roaming charges with overseas data management controls (not a problem in a Covid world sadly)
4. How to support BYOD employees while they WFH
Organisations will need to ramp up their IT technical support for working from home, as many corporate support systems do not have the human resources or tools necessary to support a fully BYOD setup. As we settle into a sustained period of remote work, IT leaders will need to assess their ability to respond remotely to employee connectivity issues.Support personnel will need visibility of the employee's digital experience to understand where productivity is being impacted by poor network or application performance. A global leader in digital experience monitoring is Sinefa.
Some UEM environments, such as VMware Workspace ONE and Microsoft Intune allow some remote management of devices.
BYOD policies do not just cover IT-focused issues. Other groups such as HR, legal and accounting should all contribute components of any BYOD or WFH strategy.
5. Consider outsourcing UEM and MTD builds and management
UEM builds and management are a specialist capability. MobileCorp offers a professional service for UEM build and deployment, and ongoing managed services across all the leading UEM vendors including VMware Workspace ONE, Microsoft Intune, MobileIron, SOTI and Jamf.
We have thousands of devices under management for Australian enterprise and business customers.
From building a UEM instance, through testing and deployment, to ongoing management and service desk, MobileCorp has accredited highly skilled UEM engineers to deliver your UEM environment.
Our UEM managed service includes:
- audit and remediation of existing instances
- design and build of new instances, configuration of profiles
- deployment of environment, enrolling and deploying bulk devices
- security management including device wipe, kiosk mode, profile sync
- remote application management
- proactive monitoring and technical support service desk
- data and asset management and reporting
- solution consultancy
- licensing
- solution implementation
- integration with your UEM environment
- integration with identity and access management (IAM) solutions and single sign-on (SSO)
We also offer an ongoing managed service to monitor, manage and provide relevant reporting from the Wandera environment.
e. phill.mcsherry@mobilecorp.com.au
m. 0419 173 333
About MobileCorp
MobileCorp is an enterprise ICT solutions company with a mission to deliver our customers a communications technology edge. We provide Managed Mobility Services, Enterprise Mobility Management, Complex Data and IP Networks, and Unified Communication solutions. We have a proven track record providing managed services for Australian enterprise and business, and we are a Telstra Platinum Partner.
UEM Michelle Lewis 25 Aug 2020
Related Posts
Popular Tags
- Mobile Devices (82)
- Mobility (81)
- Telstra (66)
- 5G (65)
- MobileCorp Managed Services (55)
- Mobile Network (38)
- Networks (34)
- Cradlepoint (32)
- Apple (29)
- MobileCorp (29)
- iPhone (25)
- Remote Working (23)
- Network (17)
- Covid-19 (16)
- Mobile Security (15)
- Wireless WAN (15)
- Cyber Security (14)
- UEM (14)
- MDM (11)
- Mobile Expense Management (10)
- Mobile Device Management (9)
- TEMs (9)
- Mobile Device Lifecycle (8)
- Cloud (7)
- Unified Comms (7)
- Unified Communications (7)
- Wandera (7)
- Android (6)
- Sustainability (6)
- Data Networks (5)
- Network Security (5)
- Samsung (5)
- Security (5)
- Digital Experience (4)
- IOT (4)
- Microsoft Intune (4)
- Blog (3)
- IT Services (3)
- Microsoft (3)
- Data (2)
- Government (2)
- Microsoft 365 & Teams (2)
- Retail (2)
- nbn (2)
- webinar (2)
- 4G (1)
- DAS (1)
- EMM (1)
- Emerging Technologies (1)
- Hosted Telephony (1)
- Managed Desktops (1)
- SD-WAN (1)
- Starlink (1)
- Telstra Services (1)
- WWAN (1)
- video (1)








