Jamf Endpoint Security
It doesn’t matter how locked down your network is,
if you have unsecured mobile devices sitting outside and accessing the network,
- the risk is real.
Enquire Now




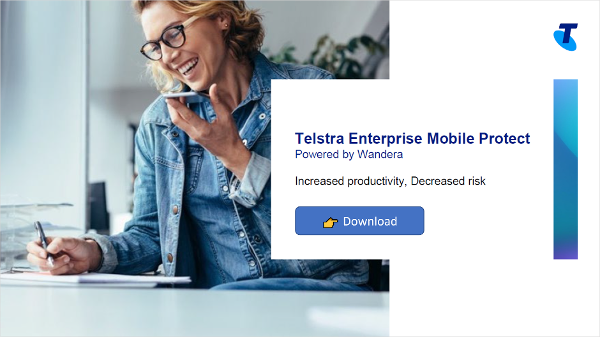
MobileCorp, Telstra and Jamf Endpoint Security
MobileCorp offers Jamf Endpoint Security as a Telstra value-add service - known as Telstra Endpoint Mobile Protect and paid through your Telstra bill - or as a standalone modern security solution.
We offer professional services including:
- solution architecture
- licence procurement
- instance build
- onboarding
- integration with a UEM environment
- integration with identity and access management (IAM) solutions and single sign-on (SSO)
We also offer an ongoing managed service to
- monitor the instance and respond to alerts
- manage users
- report on threats, vulnerabilities, compliance, data usage
- manage policy changes


What is Jamf Endpoint Security?
There are three Jamf security solutions, designed to manage and protect Apple-centric fleets (also works with non-Apple devices). These solutions are also sold through Telstra as Telstra Endpoint Mobile Protect.
Jamf Protect - Comprehensive endpoint security, threat defense, web threat prevention and content filtering. Telstra refers to this service as Mobile Threat Defence.
Jamf Connect - Modern and secure access to applications and resources with one set of cloud identity credentials and a ZTNA solution to replace legacy VPNs.
Jamf Safe Internet - This solution is aimed at students in education settings. It combines network threat prevention and content filtering to protect students and devices— stopping security threats before they start.
Jamf Protect
Telstra refers to this service as Mobile Threat Defence.
Jamf Protect makes responding to incidents easy by isolating malicious software, eradicating unwanted files and getting devices back into a trusted state automatically, causing no downtime for the user.
There are five key component features to Jamf Protect.
- Detection and Alerts: Real-time detection of malicious applications, scripts and user actions.
- Threat Prevention: Jamf Protect quarantines known malware, adware and ransomware; and also prevents some unknown threats from running. It locks Command and Control (C2) traffic and risky domains. This prevents zero-day phishing attacks and communication with malicious servers.
- Monitor and Remediate: Granular insights into endpoint activity.
- Compliance: Real-time visibility for IT teams, App insights, benchmarking and regulatory compliance covered.
- App Integrations: Level up with app integrations, API access and more.
Detections and Alerts
Jamf Protect's endpoint security for Mac adapts to your environment and minimises risk for your users, endpoints and company data— flagging concerns across Mac and mobile devices.
- Behavioral analytics identify suspicious or malicious activity.
- Customised analytics adapt Jamf Protect’s analytics to your unique needs.
- Threat hunting allows you to hunt for threats that specifically target your environment.
- The MITRE ATT&CK framework maps activity through core analytics.
Threat Prevention
Each attack puts your company data at risk—layer security by protecting the user, the endpoint and your network activity.
- Removable storage controls help prevent data loss.
- Advanced machine learning and threat intelligence engine MI:RIAM identifies and prevents zero-day phishing attacks.
- In-network protection blocks ransomware, crypto-jacking and malicious domains in real time before they impact devices.
- Real-time insights into risks allow IT to configure automated mitigating policy actions.
- Online privacy safeguards with encryption protect against personal data collection and phishing.
- Advanced privacy features ensure that security doesn’t infringe on your users’ personal privacy.
- Device security protects all devices, whether company-owned or BYOD.
- On-device content filtering uses Apple technology to filter content directly on supervised iOS and iPadOS devices.
Monitor and Remediate
Granular insights into endpoint activity. Jamf Protect's mobile security management and Mac endpoint protection offers:
- Device health and compliance: receive immediate alerts when devices deviate from your OS hardening configurations.
- macOS security tool visibility: at-a-glance activity and updates for built-in macOS security tools like XProtect, Gatekeeper and MRT.
- Unified log forwarding: a customisable feed of Unified Log data from macOS to your system-of-record for visibility and compliance.
- CIS benchmarks: enforce and monitor a secure baseline for adherence to CIS macOS benchmarks.
- Device risk: monitor the overall threat flow and understand the risk posture of your entire fleet.
- Powerful response: perform incident response manually or automate workflows with Jamf Pro: the tool that IT already uses to manage Mac.
Compliance
Meet and maintain compliance requirements.
- Real-time visibility: view compliance and endpoint telemetry activity data in Jamf Protect. Data analysis tools allow IT and security teams to immediately investigate, mitigate or remediate issues as needed.
- Regulatory compliance: align your deployment with CIS benchmarking standards out-of-the-box.
- App Insights: monitor for the presence of non-compliant or risky apps that could put organizational or personal data at risk.
App Integrations
Jamf Protect and Jamf Pro work with apps you already know and trust.
Minimise risk by reporting to your SIEM, managing your enterprise's authentication process through your Identity Provider (IdP) and displaying endpoint health data on customized dashboards.
Extend Protect with more capabilities.
Unlock powerful workflows by combining Jamf with third-party solutions from Jamf Marketplace. Extend real-time notifications to your smartphone or other mobile devices. Forward rich Apple endpoint data to your SIEM or EDR to provide the most comprehensive data visualization.
Offering powerful API access.
Integrate Jamf Protect into custom tools and workflows with a robust API that uses GraphQL. IT Admins and InfoSec can easily query content and make modifications to support your organization’s unique needs.
End-to-End Protection with Wandera and MobileCorp
MobileCorp’s preferred mobile security and data policy compliance vendor, is Wandera.
There are three critical components to the Wandera solution:
- Mobile Threat Defence – effective endpoint security and real-time prevention of network attacks
- Mobile Data Policy – enforce acceptable use and prevent excessive data usage
- Conditional Access – zero trust network access
Jamf Connect
Telstra refers to this service as Data Policy.
Make Zero Trust Network Access a reality.
Jamf Connect builds on identity management by offering modern remote access with Jamf's next-generation VPN applying Zero Trust principles to native Apple frameworks for managed or BYOD devices.
Boost employee productivity without sacrificing safety.
Access Policies
- Build granular access policies to ensure that only safe devices can access corporate applications and data.
- Create access policies for individual on-prem or SaaS applications.
- Ensure only trusted users on safe devices —both corporate and personally owned— can access the specific apps they need for work.
Zero Trust Deployment
With Jamf Connect, a user can unbox their device, power it on and access all of their corporate applications and resources after signing on with a single set of cloud identity credentials.
All on an Apple device that has world-class privacy protections.
Key Features
Account creation and authentication: create secure accounts that get users up and running immediately with a single set of cloud identity credentials. Users can securely access devices and resources from anywhere, with the added protection of multi-factor authentication.
Identity-centric security model: only authorized users can connect. They benefit from consistent policy enforcement across data centers, clouds and SaaS applications. Single sign-on (SSO) eliminates certificate management.
Risk-aware access policies: enhance security by preventing access from users and devices that may be compromised.
Fast and efficient connectivity: access business apps without impacting battery life. Jamf operates in the background without interfering with the user experience.
Intelligent split tunneling: ensure secure business connections while enabling non-business applications to route directly to the internet. This preserves end-user privacy and optimises network infrastructure.
End-to-End Protection with Wandera and MobileCorp
MobileCorp’s preferred mobile security and data policy compliance vendor, is Wandera.
There are three critical components to the Wandera solution:
- Mobile Threat Defence – effective endpoint security and real-time prevention of network attacks
- Mobile Data Policy – enforce acceptable use and prevent excessive data usage
- Conditional Access – zero trust network access
Jamf Security for Telstra customers
Leverage MobileCorp’s expertise as a Telstra Platinum Partner to understand the options for purchasing Jamf with Telstra.
Through MobileCorp, Telstra customers can secure special promotional pricing, and unique service bundles.
Telstra customers may also be eligible to use Loyalty funds for Jamf licensing and MobileCorp Jamf professional and managed services.
** JAMF BUSINESS PLAN **
MobileCorp can also leverage a unique Jamf Business Plan solution for Telstra customers which includes Jamf Protect, Jamf Connect and also Jamf Pro, which is an MDM solution. Learn more.
Our Tech Partners
Leaders we are proud to partner with.





















News and Insights from MobileCorp
Mobile Endpoint Security
Speak to our MobileCorp Representative
To get started with a technology solution, call us on 1800 243 252
Enquire Now