With an EMM solution in place can you put a big tick next to mobile device defence? It would be a brave CISO who did.
In the current political climate and with the volume of cyber attacks on Australian organisations increasing, surely every corporate in Australia is currently reviewing its cyber security defences.
Is EMM enough for mobile device defence?
One subject that keeps being raised with MobileCorp around mobile security is whether having an EMM solution, like VMware Workspace One, or Microsoft Intune, or Jamf, is sufficient to defend against cyber attack.
Here are the top four questions we are being asked....and responses by MobileCorp CTO, Phill McSherry.
1. Doesn’t my EMM environment already provide mobile security?
The short answer is no. EMMs are primarily a device configuration system, with security focused on restricting what the end user can do on the device rather than providing threat detection. EMMs that do have the ability to perform content filtering on websites rely on an administrator to continuously maintain a blacklist or whitelist of sites that they must curate themselves.
2. What are the security features included in my EMM environment?
While this varies depending on the EMM environment and the devices enrolled, generally EMM security falls under the following:
- Restricting features such as the camera, Bluetooth, or end users downloading applications
- Enforcing features such as passcodes, the inability to remove corporate apps, or what Wi-Fi the end user can connect to
- Disabling a device if lost or stolen
3. What can MTD solutions offer that EMM can’t?
MTD can scan and protect against malicious apps, crypto jacking, man in the middle attacks, and block phishing websites, malware traffic and spam websites. They can also detect and protect against app and web data leakage, zero day phishing attacks, as well as dynamically filter web content.
4. Do I really need mobile security? What is the business case?
When people ask me this question I usually ask them two in return?
- Do you have a firewall on your PC?
- Do you have threat detection on your network?
If so, why would you not extend the same protection to mobile devices that are part of your network?
Employees assume corporate devices are secure
When employees are using a corporate device they assume the company has taken security precautions. If employees are aware that the company is managing the device using EMM, they are even more likely to assume it is secure and they do not need to worry.
MTD is looking where EMM is not
Employees are increasingly completing more and more of their work on mobile devices. Some roles - the road warriors in sales and field force staff - are completing the majority of their work on mobile, or would like to be.
A lot of apps on mobile devices have credentials stored in them. These apps generally pass through those credentials to a website and that is where threat detection comes in. A mobile threat defence solution scans those apps, and the traffic from them looking for vulnerabilities.
An example would be an employee receiving an email purporting to be from their bank and clicking through to a fake website. A Mobile Threat Defence solution would stop the employee from going to website or delivers a warning - depending on how the MTD has been set up. An EMM solution won't do that unless the administrator has specifically manually blocked that particular website.
Another example would be if a banking app is leaking data or an app is scraping passwords, MTD will detect that whereas EMM is not even looking for it.

Better together - EMM and MTD
Many MTD solutions have been designed to work in tandem with EMM solutions, integrating the strengths of multi-level visibility with a sophisticated array of tools to control and adjust devices. With the combined power of both technologies, new insights on the security and status of every device can be surfaced at the device, application, infrastructure or data level. These insights can then be responded to using the functionality of either platform.
Examples:
- MTD detects a hacker attempting a man-in-the-middle attack
- EMM restricts compromised devices, blocks network access or selectively wipes corporate data
- EMM detects rogue profile configuration
- MTD alerts admins and end users. Blocks relevant traffic across both app and browser
Comparison of Features
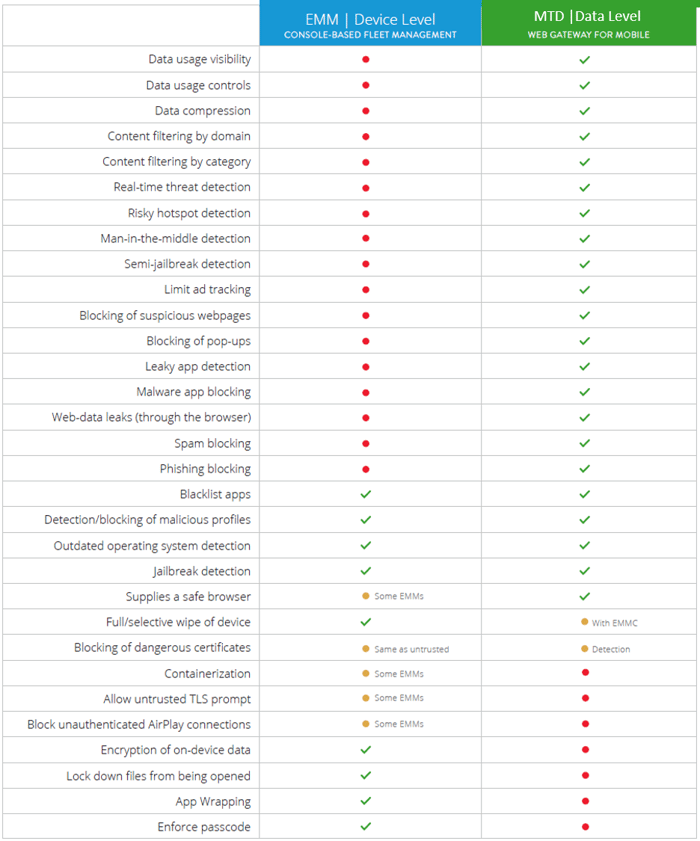 Credit: Wandera
Credit: Wandera
Learn more about Mobile Security solutions
Learn more about EMM
About MobileCorp
MobileCorp is an enterprise ICT solutions company with a mission to deliver our customers a communications technology edge. At MobileCorp we believe in being at the forefront of ICT technology shifts so that we can bring trusted insights and innovative solutions to our customers.
We provide Managed Mobility Services, Enterprise Mobility Management, Complex Data and IP Networks, and Unified Communication solutions. We have a proven track record providing managed services for Australian enterprise and business, and are a Telstra Platinum Partner.
Mobile Devices Michelle Lewis 30 Jun 2020
Related Posts
Popular Tags
- Mobile Devices (82)
- Mobility (81)
- Telstra (66)
- 5G (65)
- MobileCorp Managed Services (55)
- Mobile Network (38)
- Networks (34)
- Cradlepoint (32)
- Apple (29)
- MobileCorp (29)
- iPhone (25)
- Remote Working (23)
- Network (17)
- Covid-19 (16)
- Mobile Security (15)
- Wireless WAN (15)
- Cyber Security (14)
- UEM (14)
- MDM (11)
- Mobile Expense Management (10)
- Mobile Device Management (9)
- TEMs (9)
- Mobile Device Lifecycle (8)
- Cloud (7)
- Unified Comms (7)
- Unified Communications (7)
- Wandera (7)
- Android (6)
- Sustainability (6)
- Data Networks (5)
- Network Security (5)
- Samsung (5)
- Security (5)
- Digital Experience (4)
- IOT (4)
- Microsoft Intune (4)
- Blog (3)
- IT Services (3)
- Microsoft (3)
- Data (2)
- Government (2)
- Microsoft 365 & Teams (2)
- Retail (2)
- nbn (2)
- webinar (2)
- 4G (1)
- DAS (1)
- EMM (1)
- Emerging Technologies (1)
- Hosted Telephony (1)
- Managed Desktops (1)
- SD-WAN (1)
- Starlink (1)
- Telstra Services (1)
- WWAN (1)
- video (1)







