The cracks were appearing before the pandemic, and the mass shift to remote working has now broken the enterprise perimeter. Organisations should trust no one and move urgently to a zero trust posture.
- Remote work shift drives ZTNA adoption
- Gartner recommends ZTNA pilot
- Start with Zero Trust
- The Principles of Zero Trust
- Flavours of ZTNA
- Gartner: How to evaluate a ZTNA vendor
- Wandera Private Access
Remote work shift drives ZTNA adoption
The recent shift to a pandemic-inspired remote workforce has accelerated the adoption of Zero Trust Network Access (ZTNA), says research consultancy, Gartner.
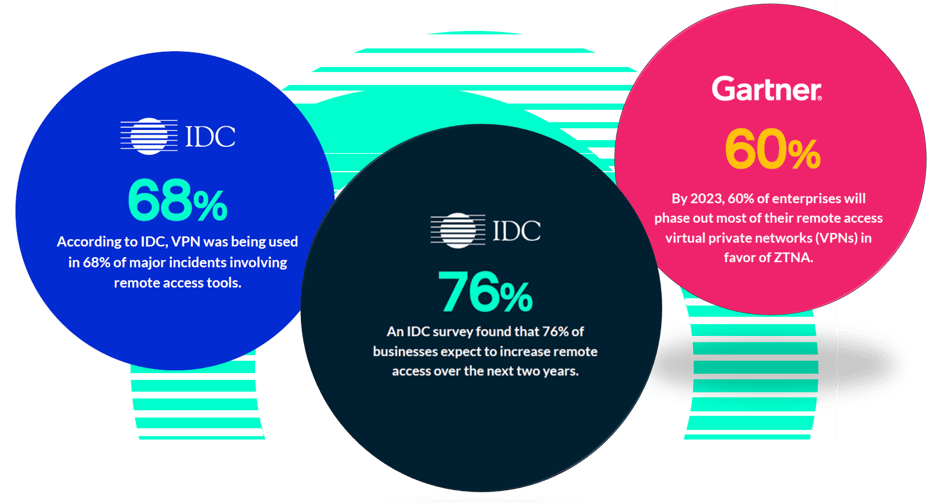
ZTNA addresses concerns over cyber threats, end user digital experience, IT visibility and control, and the hardware and bandwidth limitations of traditional VPN access.
As more organisations transition to remote work, ZTNA has piqued the interest of organisations seeking a more flexible alternative to VPNs and those seeking more precise access and session control to applications located on-premises and in the cloud.
Gartner Market Guide 2020
Gartner recommends ZTNA pilot
Gartner released a ZTNA Market Guide in June 2020 as the pandemic was at its peak across the US. The guide called on IT leaders to budget and pilot a ZTNA project to demonstrate the benefits of ZTNA across an organisation.
ZTNA augments traditional VPN technologies for application access, and removes the excessive trust once required to allow employees and partners to connect and collaborate.
Security and risk management leaders should pilot ZTNA projects as part of a SASE strategy or to rapidly expand remote access.
The Guide advises that if VPN replacement is the primary goal, organisations should plan to retain the VPN for a period of time, while verifying that the ZTNA product can replace all use cases for the VPN. This will allow latency testing of the ZTNA product for remote workers ensuring that ZTNA-delivered application latency be no worse than the existing VPN.
Gartner also advises role-based access control (RBAC) to avoid allowing all users to access all applications except in the observation phase to build policies. Applications and workflows that are not candidates for ZTNA should be identified and excluded from the scope. This includes access to and download of unstructured data and consumer-facing applications.

Start with Zero Trust
Zero Trust Network Access (ZTNA) is an IT security model that requires strict verification of every individual and device that attempts to access sensitive resources on the network, no matter where they are located.
ZTNA starts with a default deny posture of zero trust. It grants access based on the identity of the humans and their devices, plus other attributes and context - such as time, date, geolocation and device posture - and offers the appropriate trust required at the time.
The result is a more resilient environment, with improved flexibility and better monitoring. ZTNA reduces the surface area for cyberattack.
The Zero Trust Network Access (ZTNA) model was created in 2010 by John Kindervag, who at the time was a principal analyst at Forrester Research. His concept was based on the realisation that traditional security models operate on the outdated assumption that everything inside an organisation’s network should be trusted.
"Zero Trust is a simple concept. We eliminate the concept of trust within the network. We say there are no more trusted interfaces. No more trusted users. No more trusted packets. No more trusted applications. By eliminating the concept of trust we can simplify how we do network security."
John Kindervag
ZTNA will appeal to organisations looking for more-flexible and responsive ways to connect and collaborate with their digital business ecosystems, remote workers and partners.
The Principles of Zero Trust
Zero trust as a concept has been around for ten years and for the past five it has been a network security buzzword. Now, with the sudden mass shift to remote, the concept has gained further traction and is widely accepted and increasingly embraced by IT leaders as the cybersecurity posture that should be adopted by organisations.
Kindervag outlined three main concepts to his security model
- secure access from all locations
- access control is on a "needs to know" basis and strictly enforced
- and inspect and log all traffic.
Wandera, a leading ZTNA provider elaborates with its five principles:
1. Never trust, always verify
The philosophy behind a Zero Trust network assumes that there are attackers both inside and outside of the physical network, so all users and devices must prove their trustworthiness all of the time.
2. Verify identity claims
The identity and authentication of an end user is a cornerstone of Zero Trust security. Early forms of multi-factor authentication required users to enter a one-time use code in addition to their password to prove that they were who they claimed to be. More modern approaches to authentication use other forms of verification that are more streamlined and less onerous on the user, such as possession of a specific mobile device or Single Sign On (SSO).
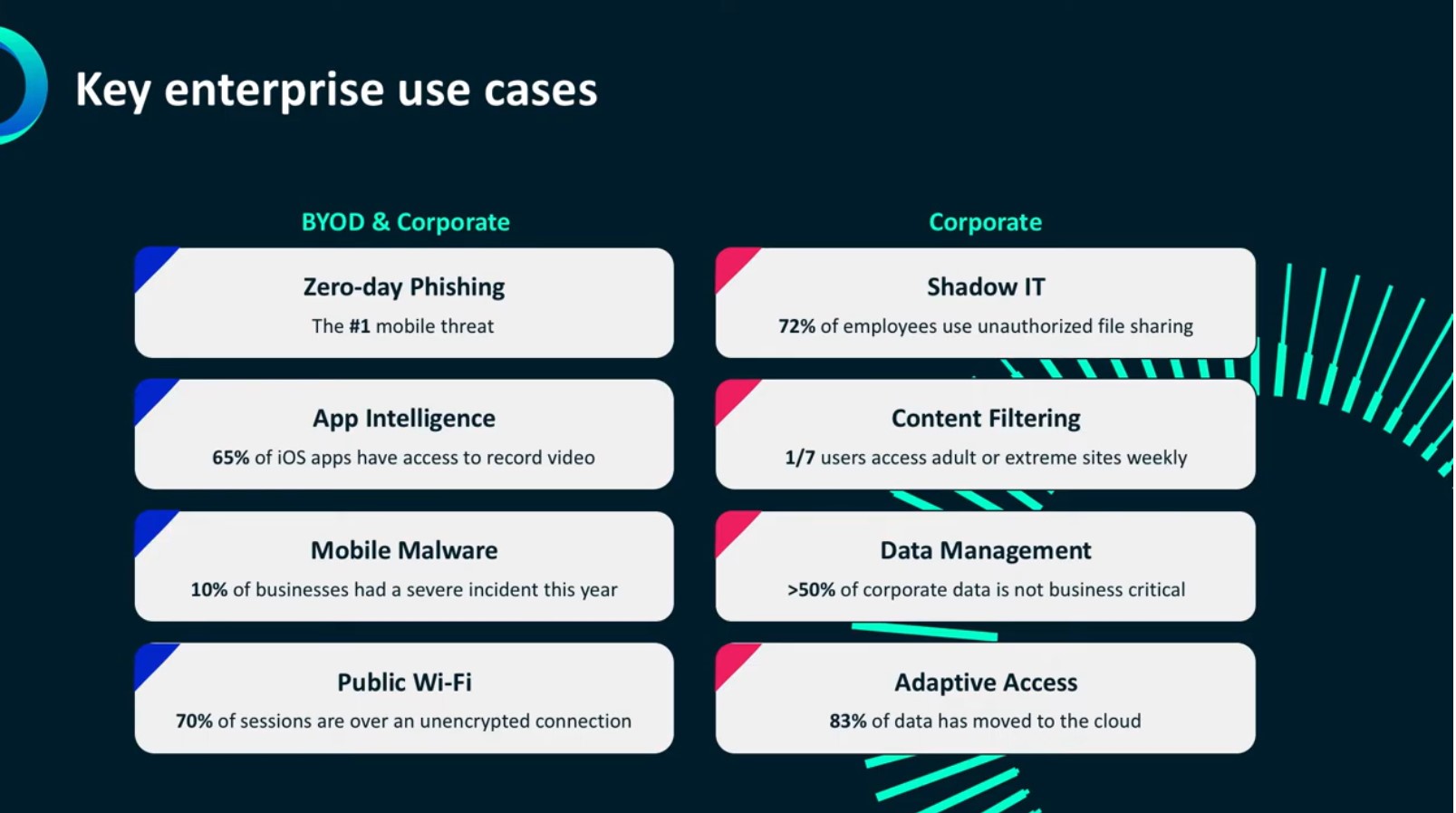
 Source: Wandera
Source: Wandera
3. Give those you know only what they need
Zero Trust security is built on the principle of least-privilege access. This means giving users only as much access as they need. This minimises each user’s exposure to sensitive parts of the network, reducing the impact that a breach can have on the organisation.
4. Do not ignore the device
In addition to strict controls on user access, Zero Trust Network Access systems must be device-aware and require assurances that every device is authorised. By denying connections from anonymous devices the attack surface of the network is further minimised. More advanced Zero Trust security models incorporate a risk assessment of the device, leaving nothing to chance.
5. Play zone defence
Zero Trust Network Access security relies on micro-segmentation to create security perimeters to break up the network into per application zones. Before connecting to an application, the user and device must authenticate and verify they have permission to access that specific application. For example, an organization with multiple applications being maintained by IT would use micro-segmentation to force users, devices, or workloads to be authorized separately for each application they access.
Flavours of ZTNA
As a Service or Standalone
ZTNA products and services are offered by vendors in one of two ways:
- As a service from the cloud
- As a stand-alone offering that the customer is responsible for supporting
Cloud-based As-a-Service is rapidly outpacing the stand-alone model. Gartner estimates that more than 90% of clients are implementing the As-a-Service model.
As-a-Service offerings require less setup and maintenance than stand-alone offerings. They typically require provisioning at the end-user or service side and route traffic through the vendor’s cloud for policy enforcement.
The stand-alone flavor appeals primarily to enterprises that are cloud-averse.
An emerging hybrid approach with cloud and on-premises access brokers is a third option appealing to organisations that want to optimise application policy rules applied for both remote and local access to applications. Stand-alone offerings require customers to deploy and manage all elements of the product.
Endpoint-initiated or Service-initiated
ZTNA products also tend towards either
- endpoint-initiated
- service-initiated
Endpoint-initiated ZTNA
An agent is installed on authorised end-user devices which sends information about its security context to a controller. The controller prompts the user on the device for authentication and returns a list of allowed applications. After the user and device are authenticated, the controller provisions connectivity from the device through a gateway that shields services from direct internet access. The shielding protects applications from denial of service (DoS) attacks and other threats they would bear if they were placed in a traditional DMZ. Some products remain in the data path once the controller establishes connectivity; others remove themselves. Endpoint-initiated ZTNA is difficult, if not impossible, to implement on an un-managed device, because of the requirement to install some form of agent or local software.
Service-Initiated ZTNA
A connector installed in the same network as the application establishes and maintains an outbound connection to the provider’s cloud. Users authenticate to the provider to access protected applications. In turn, the provider validates the user with an enterprise identity management product. Only after validation succeeds will traffic pass through the provider’s cloud, which isolates applications from direct access via a proxy. Enterprise firewalls require no openings for inbound traffic. However, the provider’s network becomes another element of network security that must be evaluated. The advantage of service-initiated ZTNA is that no agent is required on the end user’s device, making it an attractive approach for un-managed devices.
![]()
Gartner: How to evaluate a ZTNA vendor
The ZTNA market is still emerging, says Gartner, who recommends that organisations should sign only short-term contracts of no more than 12 to 24 months to retain greater vendor selection flexibility as the market grows and matures.
They also outline the following advice:
- For most digital business scenarios, favor vendors that offer ZTNA as a service for easier deployment, higher availability and protection against DDoS attacks.
- Favor vendors that require no openings in firewalls for listening services (inbound connections), which is typical for most as-a-service flavors of ZTNA.
- When security requirements demand an on-premises installation of a ZTNA product, favor vendors that can reduce the number of firewall openings as much as possible.
- If un-managed devices will be used by named users, plan to deploy a reverse-proxy-based ZTNA product or service to avoid the need for agent installation.
- Ensure that the vendor supports the authentication protocols the organisation and partners use now, including the enterprise’s standard identity store, as well as any it expects to use in the future. The wider the available range, the better, including cloud SSO providers and SaaS-delivered access management providers.
- Don’t expect partners to use your identity store. Require support for SAML, OAuth, OIDC and similar identity federation capabilities.
- Evaluate the effectiveness of a vendor’s ability to query other kinds of device agents, such as UEM, EDR and mobile threat defense (MTD), to gain additional context for improved adaptive access decisions.
- Attackers will target ZTNA trust brokers. For cloud-based offerings, evaluate their DoS and failover architectures. Require vendors to support high levels of security and monitoring for administrator accounts.
- For on-premises ZTNA products, harden the host OSs using a cloud workload protection platform (CWPP) tool that supports on-premises deployments. Rely primarily on a default deny stance with allow-listing to explicitly define the code permitted to execute on the system. Don’t rely solely on patching to keep the system hardened.

Wandera Private Access protects Australian business
Wandera Private Access is one of the ZTNA products included in the Gartner ZTNA Market Guide. Wandera has an Australian presence with an office in Melbourne.
Private Access is Wandera's cloud-hosted service that provides secure remote access to applications using ZTNA principles, whether those applications are hosted in the data centre or in the cloud.
Dynamic scaling - Being a cloud service, WPA requires no on-premise equipment. The service edge dynamically scales to handle unlimited client connections. WPA avoids the cost of full tunnelling all traffic, but without losing visibility and control of what is being accessed i.e. policy without routing.
Adaptive Access - Wandera Private Access (WPA) eliminates the broad discoverability and reachability of data and apps that users shouldn’t have access to, and limits access to specific server/application ports, reducing exposure due to server vulnerabilities. It applies adaptive access based on real-time context, to restrict access to sensitive apps and data from compromised devices.
Real Time Visibility - WPA dramatically increases visibility for admins as well as their ability to take action. They can understand who is accessing applications in real-time and identify shadow IT usage. User and app data are displayed as human-readable names, not anonymous IP addresses, while audit logs can be exported.
MobileCorp is a Wandera partner with many of our team certified as Security Masters.
Contact us to discuss ZTNA or to arrange a demonstration of Wandera Private Access.

About MobileCorp
MobileCorp is an enterprise ICT solutions company with a mission to deliver our customers a communications technology edge. We provide Managed Mobility Services, Enterprise Mobility Management, Complex Data and IP Network and Security, and Unified Communication solutions. We have a proven track record providing managed services for Australian enterprise and business, and we are a Telstra Platinum Partner. Contact Us
Remote Working Michelle Lewis 09 Sep 2020
Related Posts
Popular Tags
- Mobile Devices (82)
- Mobility (81)
- Telstra (66)
- 5G (65)
- MobileCorp Managed Services (55)
- Mobile Network (38)
- Networks (34)
- Cradlepoint (32)
- Apple (29)
- MobileCorp (29)
- iPhone (25)
- Remote Working (23)
- Network (17)
- Covid-19 (16)
- Mobile Security (15)
- Wireless WAN (15)
- Cyber Security (14)
- UEM (14)
- MDM (11)
- Mobile Expense Management (10)
- Mobile Device Management (9)
- TEMs (9)
- Mobile Device Lifecycle (8)
- Cloud (7)
- Unified Comms (7)
- Unified Communications (7)
- Wandera (7)
- Android (6)
- Sustainability (6)
- Data Networks (5)
- Network Security (5)
- Samsung (5)
- Security (5)
- Digital Experience (4)
- IOT (4)
- Microsoft Intune (4)
- Blog (3)
- IT Services (3)
- Microsoft (3)
- Data (2)
- Government (2)
- Microsoft 365 & Teams (2)
- Retail (2)
- nbn (2)
- webinar (2)
- 4G (1)
- DAS (1)
- EMM (1)
- Emerging Technologies (1)
- Hosted Telephony (1)
- Managed Desktops (1)
- SD-WAN (1)
- Starlink (1)
- Telstra Services (1)
- WWAN (1)
- video (1)