It seems every week another Australian organisation falls victim to ransomware. Why do we keep failing to secure our networks?
If it seems like every week you're hearing news of another ransomware attack on an Australian business, that's because the number of ransomware attacks in Australia have doubled in the past year.
Ransomware attacks were one of the top causes of data breaches in Australia during the first half of 2020 and the number of attacks eclipsed the total for all of 2019, according to the Australian Cyber Security Centre (ACSC).
Some victims have been large household names. Some are small private businesses. Here are a few recent examples:
- Toll Group - hit twice in 2020, first on 31 January and then again in May. The ransomware tool known as Mailto was used to launch the first attack, where hackers are believed to have used phishing emails to get into the system. The company was hacked for the second time involving ransomware known as Nefilim, and resulting in stolen data that the attacker threatened to publish if the ransom was not paid. According to Toll, the affected server contained employee information and “details of commercial agreements with some of our current and former enterprise customers”.
- BlueScope Steel - A ransomware infection was discovered in one of the company's United States-based businesses in May. The fallout impacted operations in Australia with steelmaking at Port Kembla disrupted, one mill temporarily shutdown, and many processes switching to manual operation.
- MyBudget - The Adelaide-based company blamed its breach on the sudden shift to working-from-home. The company's payment services, app, client portal and messaging services were down for days. The criminal hackers threatened to post stolen customer data on the dark web.
- Service NSW - was hacked in an attack in April 2020 that compromised 47 staff email accounts leaking the data belonging to 186,000 customers and staff. Service NSW confirmed there were 3.8 million documents stolen containing a total of 500,000 documents that included customer information.
- Levitas Capital - a Sydney hedge fund who were forced to foreclose this week after a cyber attack triggered by a fake Zoom invitation saw its trustee and administrator mistakenly approve $8.7 million in fraudulent invoices. The Fund's major client, Australian Catholic Super, withdrew its funds in the wake of the September cyber attack effectively causing the collapse of the business.
- Talman Software - an attack on the software which is used by 75 percent of the wool industry in Australia and New Zealand forced the buying and trading system offline for days. The attack encrypted files and locked down all databases disrupting the nation's wool exports which turn over between $60 million and $80 million a week.
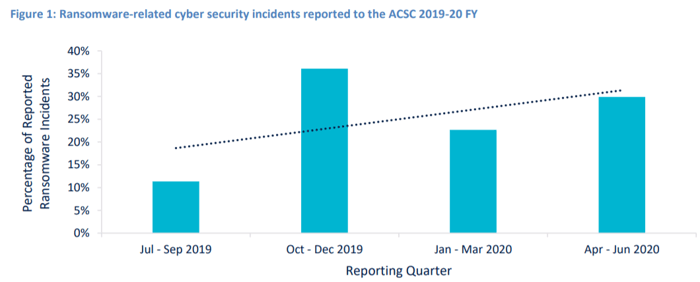
Credit: Australian Cyber Security Centre October 2020
Who is attacking us?
Recently, there has been a lot of attention on state-sponsored bad actors looking to disrupt critical infrastructure or gather information for a database on prominent citizens, but research data suggests that run-of-the-mill criminals tend to be the most common cyber threats.
Malicious actors and criminals were responsible for three in five data breaches notified to the OAIC over the first six months of 2020.
"For each state-sponsored campaign the team sees approximately four eCrime intrusions. This includes ransomware attacks, where a strain of malicious software is used to encrypt data and render it unusable or inaccessible."
Angelene Falk, Australian information and privacy commissioner.
What ransomware are we falling for?
Bad actors have used coronavirus as bait for phishing campaigns since at least March this year and the number of COVID-related scams has skyrocketed with the ACSC finding, on average, two Australians lost money or credentials to COVID scammers every day in the first half of 2020.
Ransomware attacks are now regularly stealing data from a network, rather than just encrypting it on the target network. This trend has significant implications for how organisations respond to suspected data breaches – particularly when systems may be inaccessible due to these attacks.
If you were hoping for a list of the nastiest malware, here is a mash-up of the top 5 in 2020 as suggested by multiple web sources:
| 1 | Maze |
Maze encrypts files on an infected computer’s file system and associated network file shares. Once the victim has been compromised, but prior to the encryption event, the actors exfiltrate data. After the encryption event, the actors demand a victim specific ransom amount paid in Bitcoin (BTC) in order to obtain the decryption key. An international Maze campaign targeted the healthcare sector, while its deployment in the US has been more varied. |
| 2 | REvil | REvil is a file blocking virus that encrypts victim’s files after infecting the system and sends a request message. The message explains that the victim is required to pay the requested ransom in bitcoin. If the victim fails to pay the ransom in time, the demand is doubled. |
| 3 | Tycoon | Tycoon denies access to the administrator after it infects the system, following an attack on the file servers and domain controller. It takes advantage of weak or compromised passwords and is a common attack vector that exploits servers for malware. |
| 4 | Mailto (aka Netwalker) | NetWalker harvests data then threatens to post or release the data if the target does not comply with their demands. Over the last few months, NetWalker seems to have transitioned to a RaaS (Ransomware as a Service) delivery model, selling its code to other cyber criminals. |
| 5 | EKANS | EKANS ransomware is a malware variant that infects industrial control systems to disrupt factory operations until a ransom is paid. EKANS has so far infected factories related to the automobile and electronics sector, most notably Honda. |
What industries are ransomware targets?
Anyone that stores digital information is susceptible to a ransomware incident. The size and sensitivity of information stored by an organisation is largely irrelevant. Cybercriminals may use this information to tailor their approach, however, if a cybercriminal can cause disruption by encrypting information that is of value to a victim, they will do so.
The top five sectors to report ransomware incidents to the ACSC during the 2019-20 financial year are outlined in Figure 2
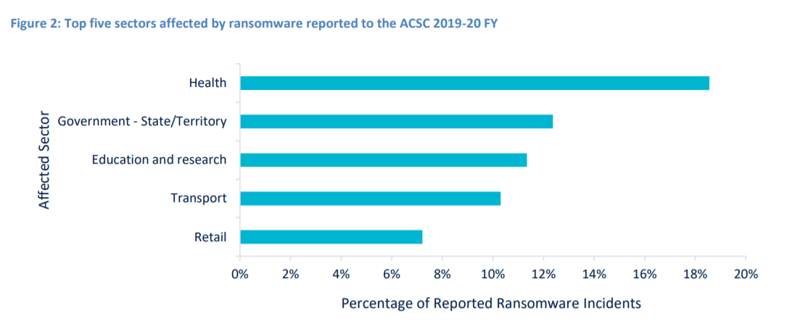
Credit: Australian Cyber Security Centre October 2020
Why are Australian businesses falling prey?
1. Pandemic WFH shift
Quick transitions to remote working have caused organisations across Australia and the world to add on new infrastructure, creating an ever-increasing attack surface for cybercriminals. Recognising the risk and acting to protect the new infrastructure is critical.
Organisations must also continue to assess and address any privacy impacts of changed business practices, both during their response to the Covid-19 outbreak and through the recovery.
2. Insufficient defence in place
Organisations must implement a layered defense system that incorporates
- basic security hygiene
- endpoint detection and response
- expert threat hunting
- strong password protocol
- employee education
There are a number of reputable threat detection and defence products in the marketplace. MobileCorp recommends Wandera for layered network, application and endpoint security. Learn more here.
3. Failure to protect data
Organisations need to have a clear understanding of how and where personal information is stored on their network, and to consider additional measures such as network segmentation, robust access controls, and encryption.
4. Failure to mitigate the human risks
Data shows that bad actors leverage valid credentials more than any other technique to gain access to a system, then persist within it, and escalate privileges.
Unfortunately, Australians have been historically terrible at spotting credential-stealing phishing attacks. Wandera have created a phishing challenge which can be used as an example of how difficult it is to spot a phishing attack.
There also needs to be a larger focus on educating employees on cyber security and privacy best practices.
Blog: Game or Shame - how to teach employees to be more cyber-aware
The risks of credential theft, abuse and phishing can be minimised by organisations adopting password managers with single sign-on and password-less multi-factor authentication to thwart password-related risks.
What to do if attacked
The ACSC advises against paying ransoms. Payment of the ransom may increase an organisation’s vulnerability to future ransomware incidents. In addition, there is no guarantee that payment will undo the damage.
Being the target of a cyber-attack is not a crime, but how an organisation responds to an attack could trigger significant legal consequences.

The business process for dealing with an attack is: contain, assess, notify, recovery.
Organisations must be able to detect and respond rapidly to data breaches to minimise the potential for serious harm.
A cyber security plan will include
- a breach assessment
- breach containment. This can mean taking systems offline.
- enacting the breach notification process if required
- a business continuity plan
- a system recovery plan
When there is malicious activity, understanding the extent of the data impacted and whether it has been copied, modified or exfiltrated is essential.
Under the Notifiable Data Breaches (NDB) scheme, organisations must notify affected individuals and the Office of the Australian Information Commissioner (OAIC) when a data breach is likely to result in serious harm to an individual whose personal information is involved and the organisation has been unable to remediate the breach.
The decision to notify or not in those circumstances will depend on a range of factors such as the nature of the personal information impacted, the remediation steps, the risk of serious harm and the ability to minimise harm if the individuals are notified.
As threat actors become more sophisticated in hiding their tracks, the assessment stage will become more complex and it may be that we see organisations opt to notifying individuals without any hard evidence of data exfiltration.
About MobileCorp
MobileCorp is an enterprise ICT solutions company with a mission to deliver our customers a communications technology edge. We provide Managed Mobility Services, Mobile Security, Enterprise Mobility Management, Complex Data and IP Networks, and Unified Communication solutions. We have a proven track record providing managed services for Australian enterprise and business, and we are a Telstra Platinum Partner.
Mobile Devices Michelle Lewis 24 Nov 2020
Related Posts
Popular Tags
- Mobile Devices (82)
- Mobility (81)
- Telstra (66)
- 5G (65)
- MobileCorp Managed Services (55)
- Mobile Network (38)
- Networks (34)
- Cradlepoint (32)
- Apple (29)
- MobileCorp (29)
- iPhone (25)
- Remote Working (23)
- Network (17)
- Covid-19 (16)
- Mobile Security (15)
- Wireless WAN (15)
- Cyber Security (14)
- UEM (14)
- MDM (11)
- Mobile Expense Management (10)
- Mobile Device Management (9)
- TEMs (9)
- Mobile Device Lifecycle (8)
- Cloud (7)
- Unified Comms (7)
- Unified Communications (7)
- Wandera (7)
- Android (6)
- Sustainability (6)
- Data Networks (5)
- Network Security (5)
- Samsung (5)
- Security (5)
- Digital Experience (4)
- IOT (4)
- Microsoft Intune (4)
- Blog (3)
- IT Services (3)
- Microsoft (3)
- Data (2)
- Government (2)
- Microsoft 365 & Teams (2)
- Retail (2)
- nbn (2)
- webinar (2)
- 4G (1)
- DAS (1)
- EMM (1)
- Emerging Technologies (1)
- Hosted Telephony (1)
- Managed Desktops (1)
- SD-WAN (1)
- Starlink (1)
- Telstra Services (1)
- WWAN (1)
- video (1)